Connecting to little devices out in the world, the ones that gather information or do specific jobs, has become a very common thing. We're talking about things like smart sensors, tiny cameras, or even parts of a bigger system that are far away. Keeping these little gadgets safe when you need to check on them or give them new instructions is, you know, really important. That's where something called an SSH key comes into the picture, especially when you're working with a platform that helps you manage these devices from a distance.
When you have many of these gadgets spread around, maybe in different buildings or even different towns, getting to them one by one to make sure they're doing okay can be quite a chore. A good remote platform helps you see everything from one spot, which is pretty handy. But, for that connection to be truly useful, it also needs to be really secure, so no one unwanted can listen in or mess with your things. That's why people often look for solid ways to make sure only the right folks get in, which is where the remoteiot platform ssh key idea comes in.
So, we're going to talk a bit about how these special keys work with systems that let you reach your far-off devices. It's about making sure your connection is private and that only you or people you trust can get access. We'll look at what makes these keys so helpful and how they fit into keeping your internet-connected gadgets safe and sound, as a matter of fact.
- Hannah Taylor Influencer Age
- Best Remote Iot Control System
- Are Ali Vitali And Jeremy Diamond Still Together
- How Old Is Nene Leakes
- Lamelo Girlfriend Latest
Table of Contents
- What's the Big Deal with RemoteIoT Platform SSH Key Access?
- How do RemoteIoT Platform SSH Keys Keep Things Safe?
- Getting Your RemoteIoT Platform SSH Key Set Up - Is It Hard?
- Why Remote Access Matters for Your IoT Gadgets
- Managing Your RemoteIoT Platform SSH Keys
- Can I Share My RemoteIoT Platform SSH Keys?
- Common Questions About RemoteIoT Platform SSH Key Use
- Keeping Your RemoteIoT Platform SSH Key Protected
What's the Big Deal with RemoteIoT Platform SSH Key Access?
You might be wondering why everyone talks so much about SSH keys when it comes to getting into your remoteiot platform gadgets. Well, think of it like this: when you want to get into your house, you use a key, right? And you want that key to be very hard for someone else to copy or guess. An SSH key for your remote devices works in a similar way, only it's for your digital front door, so to speak. It helps make sure that when your computer talks to a device far away, it's really talking to the right device, and that no one else can pretend to be you or the device. This kind of safety measure is pretty important because if someone gets into your internet-connected things, they could cause all sorts of trouble, you know.
Using these keys helps keep your information private as it travels between your computer and your far-off device. It's like having a secret code that only your computer and the device both know, which makes it very hard for anyone else to listen in on what you're doing. This means that when you send commands or get information from your remoteiot platform device, you can feel much better knowing that it's all staying between you and your gadget. It's a way to build a very private, very secure line of communication, which is, honestly, a really good thing for anyone looking after a bunch of internet-connected stuff.
How do RemoteIoT Platform SSH Keys Keep Things Safe?
So, how exactly do these remoteiot platform SSH keys manage to keep everything so well-guarded? It works with two parts: you have one part of the key that stays with you, on your computer, and another part that goes onto the device you want to connect to. These two parts are like a pair that only fit together perfectly. When you try to connect, your computer sends its part of the key to the device, and the device checks if it matches its own part. If they both fit, then the connection is allowed to happen, which is pretty clever, you know.
- T%C3%BCrk If%C5%9Fa Softwe
- Best Remote Io Raspberry Pi
- Sotwe T%C3%BCrk Ifsa
- Geoffrey Lewis Nationality
- Ammika Harris
This way of checking who's who is much, much stronger than just using a simple password, which can sometimes be guessed or figured out. With an SSH key, the chances of someone getting in without having both parts are incredibly small. It's a bit like having a very long, very complex secret handshake that only you and your remoteiot platform device know. This makes it a very reliable way to make sure that only authorized people can get to your devices, and that's a big comfort when you're dealing with sensitive information or important operations, you know.
Getting Your RemoteIoT Platform SSH Key Set Up - Is It Hard?
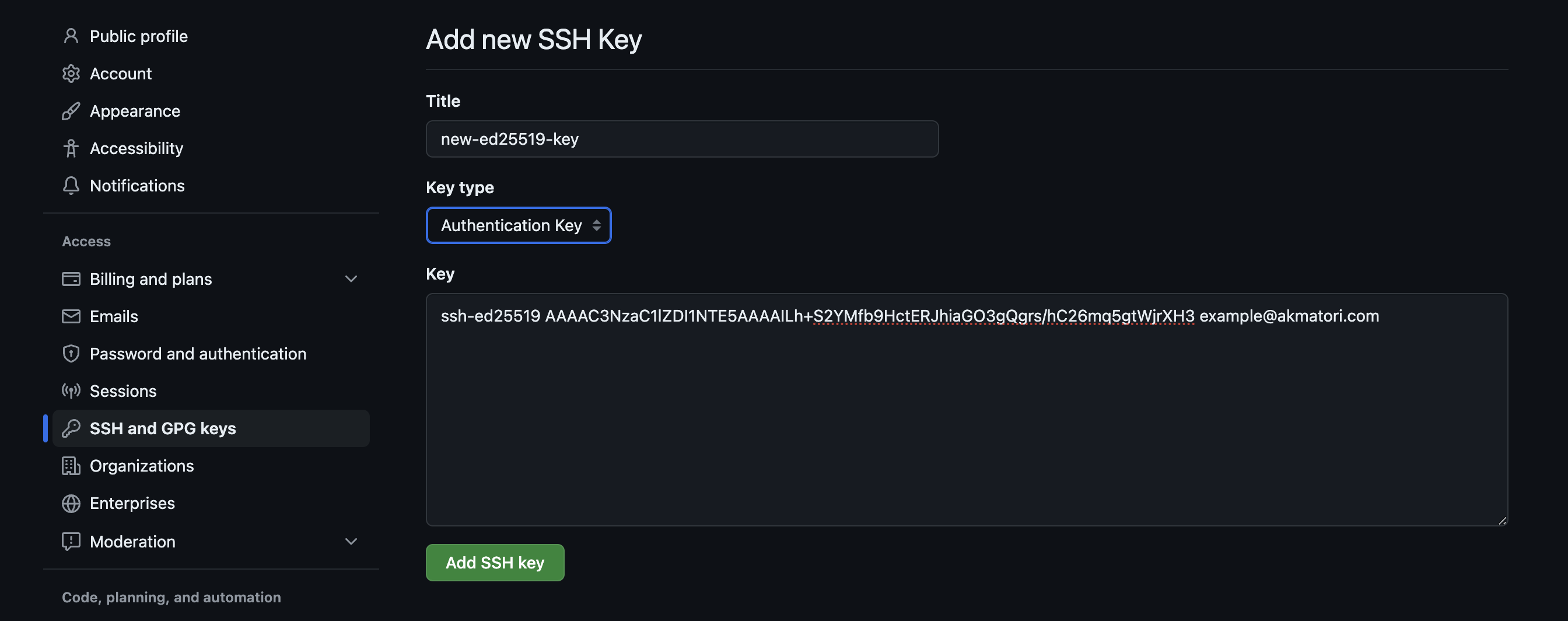
A lot of people wonder if getting a remoteiot platform SSH key ready to go is a really difficult task. The good news is, it's usually not as tough as it might sound. Most systems and platforms that help you manage internet-connected devices have pretty straightforward ways to create and put these keys in place. You often just need to follow a few steps on your computer to make the key parts, and then you put one part on your device and keep the other part safe on your own machine. It's a process that many people can do without too much trouble, so it's almost a simple thing to get done.
The platforms themselves often have helpful guides or even tools that make the whole thing quite easy to follow. They might even let you generate the key right there in your web browser and then tell you exactly where to put the public part on your remoteiot platform device. So, while it involves a few steps, it's generally a pretty smooth process that doesn't require you to be a computer wizard. It's really just about following the instructions to make sure your future connections are as safe as can be, and that's a good thing, basically.
Why Remote Access Matters for Your IoT Gadgets
Having the ability to reach your internet-connected gadgets from a distance is a really big deal for many reasons. Think about a weather sensor out in a field, or a security camera at a holiday home. You can't just walk up to them every time you need to check something or make a change. Remote access, helped by things like a remoteiot platform ssh key, means you can do all of that from wherever you are, as long as you have an internet connection. This saves a lot of time and effort, letting you keep an eye on things without having to be right there, which is pretty useful.
It also means you can react quickly if something goes wrong. If a device stops sending information, or if you need to update its settings, you can do it right away from your computer. You don't have to wait to travel to the location, which could take hours or even days. This quick response time can be really important for keeping your systems running smoothly and making sure your data is always flowing. So, in a way, remote access with good security is about making your life easier and your operations more dependable, you know.
Managing Your RemoteIoT Platform SSH Keys
Once you've got your remoteiot platform SSH keys set up, it's a good idea to know how to look after them. This means keeping your private key safe on your computer and making sure it doesn't fall into the wrong hands. Think of it like keeping your house keys in a safe place, not leaving them lying around for anyone to pick up. You might also need to add new keys if you get more devices, or remove old ones if a device is no longer in use or if someone who had access no longer needs it. This kind of upkeep is just part of keeping your system tidy and secure, basically.
Most remote platforms will give you tools to help with this. You can usually see a list of all the keys you have in use, add new ones, or take away old ones with just a few clicks. It's about having good control over who can get into your devices and making sure that access is always up to date. This makes managing your remoteiot platform ssh key setup quite simple, allowing you to stay on top of your security without too much fuss, which is pretty good.
Can I Share My RemoteIoT Platform SSH Keys?
This is a question that comes up a lot, and it's a really important one. While it might seem convenient to share your remoteiot platform SSH key with someone else who needs to access a device, it's generally not the best idea. Sharing your private key is like giving someone a copy of your only house key. If they lose it, or if it gets into the wrong hands, then your whole system could be at risk. It's much better for each person who needs access to have their own unique key pair. That way, if something goes wrong with one person's key, it doesn't affect everyone else, which is a big plus.
Most remote platforms let you set up different keys for different people, and you can even give them different levels of access. This means you can give someone just enough access to do their job without giving them full control over everything. So, instead of sharing, it's usually better to create separate keys and manage access for each individual. This keeps your remoteiot platform ssh key setup much more organized and, frankly, a lot safer for everyone involved, you know.
Common Questions About RemoteIoT Platform SSH Key Use
People often have a few common questions when they start thinking about using remoteiot platform SSH keys. One of the first things folks ask is about how long these keys last. Generally, SSH keys don't really expire on their own. You create them, and they work until you decide to remove them or replace them. However, it's a good practice to, you know, sometimes create new ones and get rid of the old ones, especially if you've had a lot of changes in your team or if you just want to refresh your security. It's a bit like changing the locks on your house every few years, just to be extra careful, basically.
Another common question is what happens if you lose your private key. If that happens, it's a bit of a problem because you won't be able to connect to your devices using that key anymore. You'd have to create a brand new key pair and then put the new public part on all your remoteiot platform devices. This is why keeping your private key very safe and maybe even having a backup in a secure place is a really good idea. It saves you a lot of hassle later on, so it's almost like having a spare tire for your car, you know.
Keeping Your RemoteIoT Platform SSH Key Protected
Keeping your remoteiot platform SSH key safe is perhaps the most important part of using them. Your private key should always be kept on your computer in a spot that's well-guarded. Many people put a password on their private key file, which means even if someone gets hold of the file, they still can't use it without that extra password. This is called a passphrase, and it adds another layer of safety, which is really smart. It's like putting your house key in a locked box, you know.
You should also be very careful about where you store backups of your private key, if you make any. Don't just put them on a regular USB stick that you might lose. Think about using encrypted storage or a very secure cloud service that you trust a lot. Regularly checking who has access to your remoteiot platform devices and making sure only the right public keys are on them is also a very good habit. It's all about being thoughtful and a little bit careful with these digital keys, as a matter of fact, because they open the door to your valuable internet-connected things.
- Raspberry Pi Remote Management Mac
- Poliana Arapiraca
- How Old Is Mike Rowe Wife
- T%C3%BCrk If%C5%9Fa Sotwe
- Fik Fap