When you think about all the clever gadgets out there, the ones that talk to each other over the internet, it's pretty amazing, isn't it? These little helpers, often called IoT devices, are everywhere, doing everything from checking your home's temperature to helping factories keep track of their stuff. But here's the thing: making sure these tiny machines stay safe and sound, especially when you're checking on them from far away, is a really big deal. It's about keeping curious eyes out and making sure only the right people, or rather, the right computers, can chat with them.
So, this is where a clever trick comes into play, something called an SSH key. Think of it like a very special digital handshake, a secret code that proves you are who you say you are, without having to shout your password across the internet. It's a way to give your remote IoT setup a little extra protection, making sure those connections are truly private and only for you. It's kind of like having a unique, super-strong lock and key for each of your little internet-connected helpers.
Many folks who look after these internet-connected devices are starting to see the true value in using these special keys, especially when they're working with a platform that helps manage everything. It's a method that just makes a lot of sense for keeping things tidy and safe, offering a way to manage who gets to speak to your devices from a distance. You know, it's almost like giving each device its own personal guard dog that only responds to your specific whistle.
Table of Contents
- What's the Big Deal with RemoteIoT Platform SSH Key Access?
- How Do SSH Keys Keep Your RemoteIoT Platform Safe?
- Getting Started with RemoteIoT Platform SSH Key Setup
- Why Should I Use RemoteIoT Platform SSH Key for My Devices?
- Putting RemoteIoT Platform SSH Key on Your Things
- What Happens if My RemoteIoT Platform SSH Key Gets Lost?
- Keeping Your RemoteIoT Platform SSH Key Protected
- The Future of RemoteIoT Platform SSH Key Security
What's the Big Deal with RemoteIoT Platform SSH Key Access?
You might be wondering why all the fuss about these SSH keys when it comes to your remote IoT devices. Well, think about it this way: your little smart home gadgets or industrial sensors are often out there, maybe in your living room or out in a field, and they need to talk back to a central spot. This chat usually happens over the internet, and that's where things can get a little tricky. If someone sneaky tries to listen in or pretend to be your device, that's a problem. So, a big deal about a remoteIoT platform SSH key access is making sure those conversations are totally private and only between your trusted system and your devices. It’s like having a special, coded language that only you and your devices understand, which is pretty cool if you ask me.
The usual way to get into things from afar often involves a username and a password. While that works, it has its weak spots. Passwords can sometimes be guessed, or even if they're super long, they might get found out if someone is really determined. This is where the SSH key method steps in, offering a much more solid way to confirm who's who. It's actually a pair of keys, a public one that you can share a bit, and a private one that you keep absolutely secret. When you use a remoteIoT platform SSH key, you're basically setting up a very strong, two-part lock system that's much harder to break into. This makes a big difference in how safe your remote connections feel, giving you a lot more peace of mind.
For those managing a whole bunch of internet-connected things, especially across different places, getting a grip on access can be a bit of a headache. The idea of a remoteIoT platform SSH key simplifies this greatly. Instead of remembering a gazillion different passwords for each device, you can use these keys to manage access in a more organized way. It means you can give different levels of access, or even take access away quickly, without having to change a bunch of passwords one by one. This centralized approach, handled by your chosen platform, just makes life easier and keeps things much more orderly. It's really about making the whole process of looking after your devices a lot less stressful, which is something we all appreciate, right?
- Geoffrey Lewis Nationality
- Eyeview Digital
- Best Remote Iot Device Solution
- T%C3%BCek If%C5%9Fa Sotwe
- Best Remote Iot Management Software
How Do SSH Keys Keep Your RemoteIoT Platform Safe?
So, how do these special keys actually work their magic to keep your remote IoT platform safe? Well, it's a bit like having a very clever secret handshake that only works if both sides have the right part of the code. When you set up an SSH key for your remoteIoT platform, you generate two pieces: one is a public key, and the other is a private key. The public key is what you put on your IoT device or the server it talks to. The private key, on the other hand, stays with you, on your computer or where you manage your devices. When you try to connect, your computer sends a request, and the device challenges it to prove it has the matching private key. This whole process happens without ever sending your secret private key over the internet, which is a very important part of its strength. It's kind of like having a secret knock that only you know, and the door only opens if you do it just right, without ever telling anyone the knock itself.
This method of connection is much more secure than simply using a password. Passwords can be guessed or even captured if someone is listening in on your network. With an SSH key, the chances of someone guessing or stealing your private key are very, very low, because it's a very long, complex string of characters that's unique to you. It's virtually impossible for someone to just stumble upon it. Plus, even if someone did get hold of your public key, it's useless without the matching private one. This means that when you're using a remoteIoT platform SSH key for your connections, you're building a much stronger wall around your data and your devices. It's a bit like building a fortress with a very intricate gate that only opens with a specific, unique key, making it incredibly difficult for unwanted visitors to get in, which is a relief for anyone with important data.
Another nice thing about using SSH keys is that they can be used for automated tasks. Imagine you have a hundred devices, and you need them all to do something at a specific time, or you need to gather information from them regularly. Instead of manually logging into each one with a password, which would be incredibly time-consuming, you can set up your remoteIoT platform SSH key to allow your management system to connect to these devices automatically. This not only saves a huge amount of time but also reduces the chance of human error. It’s a way of making your systems work smarter, not harder, which is something everyone wants, right? This automation also means that your devices can communicate with the platform without you having to be there, making the whole system more self-sufficient and reliable, in a way.
Getting Started with RemoteIoT Platform SSH Key Setup
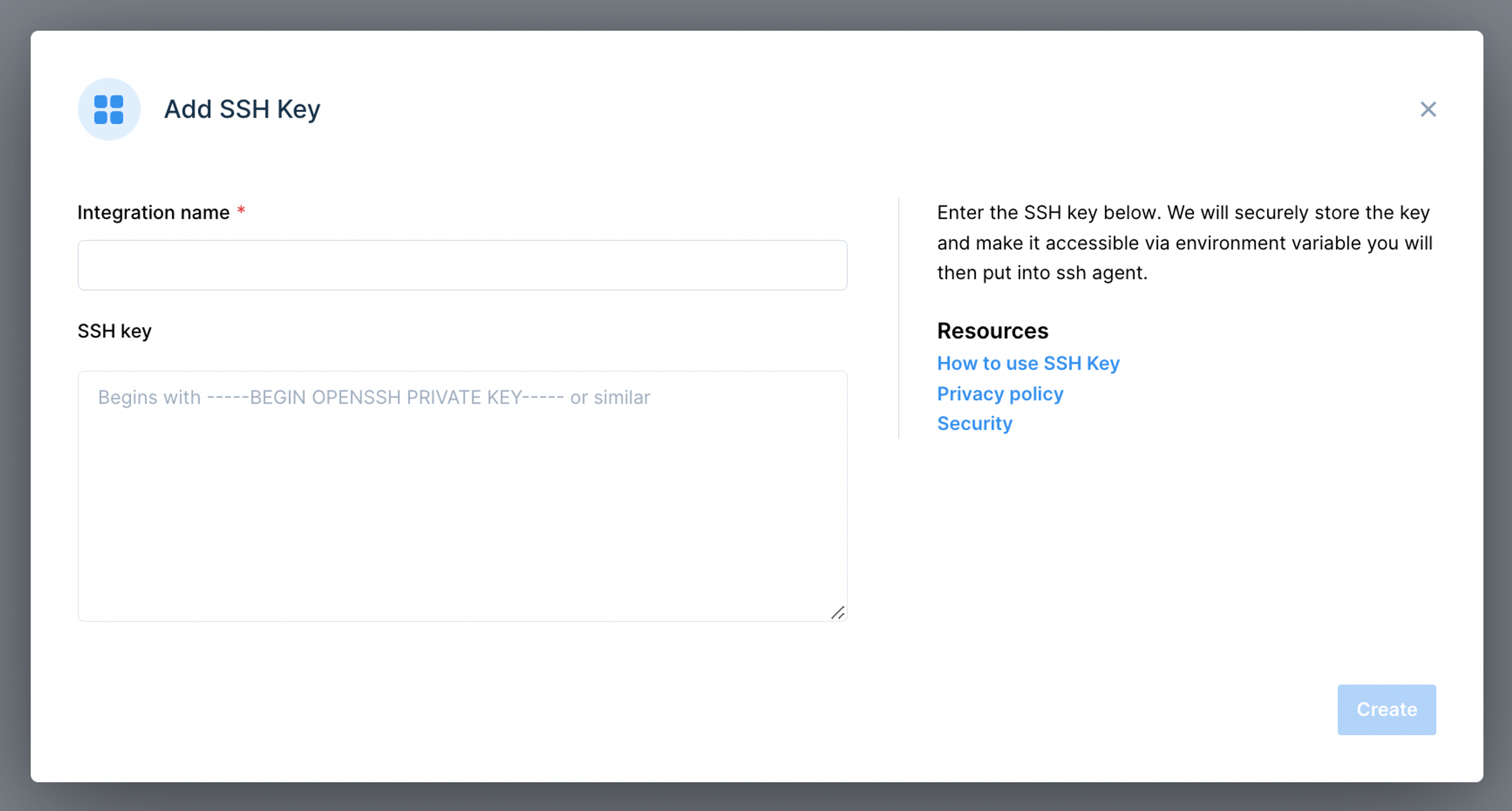
If you're thinking about using a remoteIoT platform SSH key, getting started is simpler than it might seem. The first step is usually to create these key pairs on your own computer. Most operating systems have tools built right in that let you do this with just a few simple commands. You'll end up with those two files we talked about: the public key and the private key. It's important to remember where you save them, especially the private one, because that's the piece you'll need to keep very safe. Think of it like getting a new set of house keys made; you keep one for yourself and maybe give a copy of the other part to someone trusted to let them in, but never the master key. This initial step is really about preparing your own personal access pass for your IoT world, which is a good feeling.
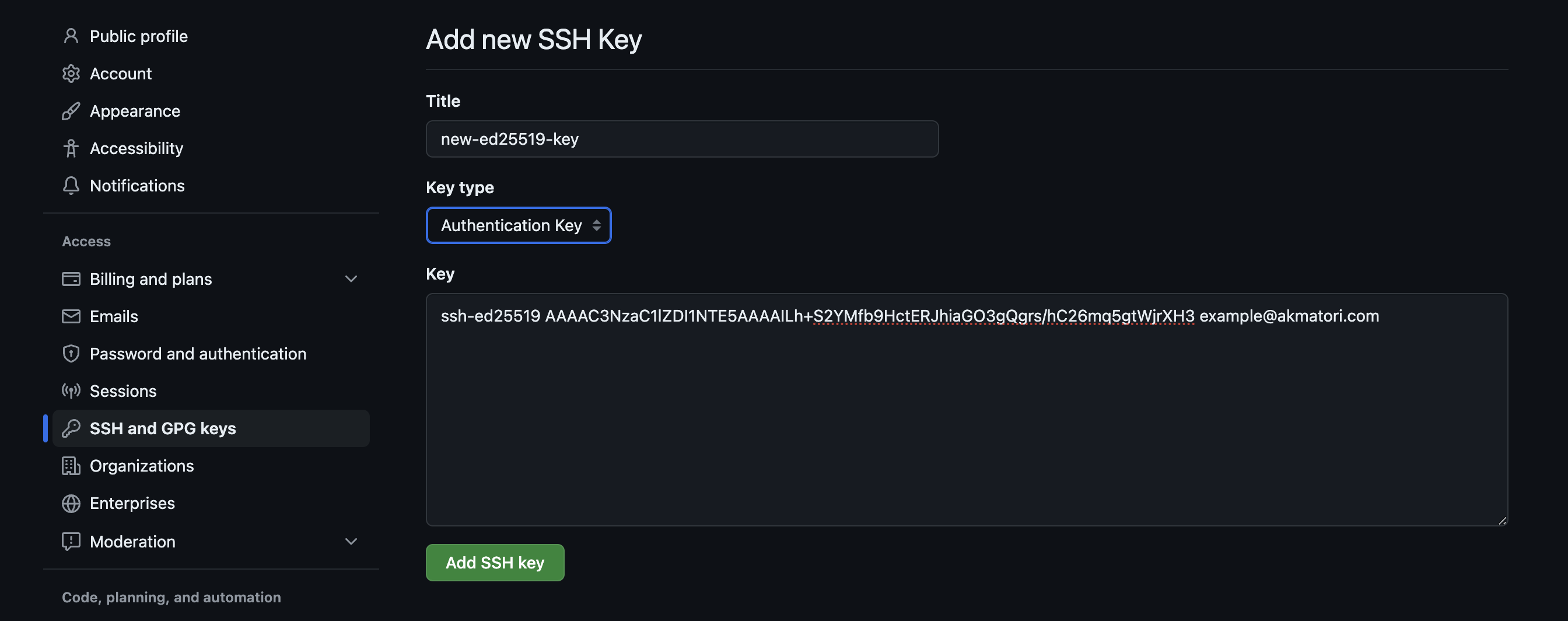
Once you have your key pair, the next bit involves telling your remote IoT platform about your public key. Most platforms that support SSH key access will have a spot in their settings or a specific part of their interface where you can upload or paste your public key. This tells the platform, "Hey, this is my official digital fingerprint. If anyone tries to connect to my devices through you, make sure they have the matching private key." It's a straightforward process, usually just a few clicks or a copy-paste job. This step basically enrolls your personal key with the system, allowing it to recognize you when you try to make a connection. It's quite easy to do, and it sets the stage for much more secure interactions with your devices, you know.
After your public key is on the platform, you'll then need to make sure your IoT devices themselves are set up to accept connections using this method. This might involve a little bit of configuration on each device, telling it to look for SSH key authentication instead of, or in addition to, a password. Sometimes, the platform helps with this step, pushing the public key directly to your devices. Other times, you might need to manually add the public key to each device's authorized keys file. It sounds a bit technical, but there are usually clear instructions for this part, and once it's done, you're good to go. This final piece of the puzzle ensures that your remoteIoT platform SSH key system is working end-to-end, creating a secure bridge between your control center and your little gadgets. It's a pretty neat way to get things talking safely.
Why Should I Use RemoteIoT Platform SSH Key for My Devices?
You might be asking yourself, "Why go through all this trouble with a remoteIoT platform SSH key when a password seems to work just fine?" Well, there are some really compelling reasons. For one, it's a huge step up in terms of keeping your devices safe from unwanted visitors. Passwords, as we've touched on, can be guessed, or even if they're very strong, they can be vulnerable to certain kinds of digital attacks. SSH keys, on the other hand, are incredibly difficult to crack. They're like super-long, random strings of characters that are practically impossible for a computer to guess in any reasonable amount of time. So, if you're serious about keeping your IoT setup private and secure, this method offers a much higher level of protection, which is something you really want to have.
Another big plus is the convenience factor, especially when you're managing a lot of devices. Imagine having to log into fifty different smart sensors, each with its own unique password, every time you need to check something or make an update. That would be a nightmare, wouldn't it? With a remoteIoT platform SSH key, you can set up your system to use the same key pair for all your devices, or at least groups of them. This means you can connect to any of them quickly and easily, without having to type in a password each time. It streamlines your workflow and makes managing your fleet of devices much more efficient. It's about making your life easier while also making things safer, which is a great combination, I think.
Beyond just security and ease of use, using SSH keys also helps with automation. Many remote IoT platforms let you set up scripts or programs that automatically connect to your devices to gather data, send commands, or perform updates. For these automated tasks to work smoothly and safely, they need a way to prove their identity without human input. An SSH key is perfect for this. You can configure your automation tools to use your private key, allowing them to connect to your devices without needing a password. This means your systems can operate around the clock, doing their job without you having to intervene. It truly makes your remote IoT setup more capable and self-sufficient, in some respects, which is a pretty powerful thing for any kind of tech system.
Putting RemoteIoT Platform SSH Key on Your Things
Once you've got your remoteIoT platform SSH key ready to go, the next practical step is getting it onto your actual devices. This part can vary a little depending on what kind of IoT gadget you have and how it's set up. For many Linux-based devices, which are quite common in the IoT world, you'll typically need to add your public key to a special file called `authorized_keys` within the SSH configuration on the device itself. This file tells the device, "Hey, if someone tries to connect with this public key, let them in without a password." It's a bit like giving a trusted friend a spare key to your house, so they can come and go as needed. This process is usually done once per device, or when you want to change who has access, which is fairly simple.
If your remote IoT platform is a bit more advanced, it might actually help you with this step. Some platforms have features that let you push your public key out to all your connected devices with just a few clicks. This is incredibly helpful if you have many devices, as it saves you the trouble of doing it one by one. It's like having a master remote control that can program all your individual gadgets at once. This kind of integration makes the whole process of securing your fleet much more manageable and less prone to errors. It's a big time-saver, and it ensures that all your devices are set up correctly from the get-go, so that’s really nice.
For devices that are a bit simpler or have very limited memory, putting an SSH key on them might involve a slightly different approach. Sometimes, you might need to include the public key as part of the device's initial software setup or "firmware." This means the key is baked right into the device's brain from the start. This method is common for devices that aren't meant to be tinkered with much after they're deployed. No matter the method, the goal is the same: to give your device a piece of your remoteIoT platform SSH key puzzle so it can recognize you and only you. It ensures that when your device tries to communicate, it's doing so with a verified source, making the connection safe and sound, which is very important for peace of mind.
What Happens if My RemoteIoT Platform SSH Key Gets Lost?
It's a fair question to ask: what if that super-secret private part of your remoteIoT platform SSH key goes missing or, even worse, falls into the wrong hands? This is a really important thing to think about. If your private key is lost or stolen, it's a bit like losing the master key to your digital kingdom. Someone else could potentially use it to access your devices, just as you would. This is why keeping your private key incredibly safe is the most important rule of using SSH keys. It should never be shared, never be stored in an unprotected place, and ideally, it should be protected with a strong passphrase, which is like a password for your private key itself. It’s almost like having a secret safe for your secret key, which adds another layer of protection, you know.
If you suspect your private key has been compromised, or if you simply lose access to it, the first thing you need to do is revoke it. This means telling your remote IoT platform and all your devices that this particular key is no longer valid. Most platforms have a way to do this quickly, often by removing the public key associated with the lost private key from your account. Once removed, that key can no longer be used to connect to your devices. It's like changing the locks on your digital doors immediately after realizing your key is gone. This swift action helps to prevent any unauthorized access and keeps your IoT setup safe. It’s a very important step to take right away, which is good to know.
After revoking the old key, you'll need to generate a brand new remoteIoT platform SSH key pair. This creates a fresh set of digital credentials for you. You'll then upload the new public key to your platform and distribute it to your devices, just as you did with the original setup. This process essentially gives you a whole new set of keys, making sure that only you have the ability to connect to your devices again. While it might seem like a bit of a hassle, it's a small price to pay for keeping your entire IoT ecosystem secure. It’s a bit like getting a whole new set of house keys and re-keying all your locks, just to be absolutely sure no one else can get in, which is pretty reassuring.
Keeping Your RemoteIoT Platform SSH Key Protected
Protecting your remoteIoT platform SSH key is truly paramount. The private part of your key pair is the crown jewel of your access system, and keeping it safe means keeping your entire IoT setup safe. One of the best ways to protect it is by using a strong passphrase when you create the key. This passphrase acts like a password for your private key file itself, meaning even if someone gets their hands on the file, they still can't use it without knowing that secret phrase. It's an extra layer of defense that is very, very important. Think of it like putting your secret key inside a locked box; you need two things to get to it: the box key and the secret key itself, which is a good way to keep things safe.
Where you store your private key also matters a lot. It should never be kept on a shared computer or in a cloud storage service that isn't specifically designed for highly sensitive information. Ideally, it should live on your main work computer, perhaps even on an encrypted drive, or on a dedicated hardware security device, if you're dealing with very sensitive systems. This ensures that even if your computer is compromised in some other way, the private key remains difficult to access. It’s about being smart with your storage, making sure your most valuable digital asset is tucked away in the safest possible spot. This attention to detail really helps in keeping your remote IoT key secure, you know.
Regularly backing up your private key, but doing so securely, is also a good practice. Imagine losing your computer; you wouldn't want to lose access to all your devices because your key was only stored in one place. When you back it up, make sure the backup is also encrypted and stored in a safe, offline location, like an external hard drive in a secure spot. And remember, never share your private key with anyone, no matter how much you trust them. If someone else needs access, they should generate their own key pair and have their public key added to your platform and devices. This way, each person has their own unique access point, and if one key is compromised, it doesn't affect everyone else's. This careful approach to your remoteIoT platform SSH key makes the whole system much more resilient, which is pretty reassuring.
The Future of RemoteIoT Platform SSH Key Security
Looking ahead, the role of the remoteIoT platform SSH key in keeping our connected devices safe is only going to grow. As more and more everyday items get smart and talk to the internet, the need for solid, dependable ways to manage and protect them becomes even more clear. SSH keys offer a tried-and-true method that has been used for years in other parts of the digital world, and their strength makes them a great fit for the special needs of IoT. We can expect platforms to make it even easier to use these keys, perhaps with more automated ways to set them up and manage them across vast numbers of devices. It's almost like building stronger, smarter digital locks for a world that's getting more connected every day, which is exciting.
We might also see new ways that remoteIoT platform SSH key systems work together with other security methods. For instance, perhaps they'll integrate more closely with biometric checks, like fingerprint scanners or facial recognition, for an extra layer of personal security when you try to use your private key. Or maybe they'll become part of even bigger, more complex security frameworks that manage access for entire organizations, not just individual users. The goal is always to make things safer without making them too difficult to use. This kind of ongoing development means that the ways we protect our IoT devices will keep getting better and better, offering more peace of mind for everyone involved, you know.
Ultimately, the continued focus on the remoteIoT platform SSH key speaks to a broader understanding that security for internet-connected devices isn't just an afterthought; it's something that needs to be built in from the very beginning. As these devices become more central to our lives and our businesses, having a reliable, strong way to control who can access them and what they can do is absolutely vital. The future will likely bring even more sophisticated ways to generate, manage, and revoke these keys, making the process even smoother and more foolproof. It’s about building a digital world where our smart gadgets can do amazing things, all while staying safe from harm, which is a goal we can all get behind, really.
So, to quickly go over what we've talked about, we've looked at why using an SSH key for your remote IoT platform is such a good idea, helping to keep your devices and data safe. We explored how these special keys work, giving you a strong way to connect without needing passwords. We also touched on getting started with setting them up, putting them on your devices, and what to do if your key ever gets lost. Finally, we considered how to keep your keys protected and what the future might hold for this kind of security. It's all about making your connected world a bit safer and easier to manage.
- T%C3%BCrk If%C5%9Fasotwe
- When Did Stephen Graham Start Acting
- Keith Sapsford
- Eyeview Digital
- Kirstentoosweet Bio