Putting together a system with many devices, especially those that talk to each other over the internet, often makes people think about how to keep everything separate and secure. It's a bit like having a house where you want certain rooms to have their own locks and alarms, even though they are all part of the same big structure. For things like smart sensors or machines that send data, making sure their communication stays private is really important, you know, for safety and peace of mind.
A Virtual Private Cloud, or VPC, comes into play here. It gives you a dedicated, isolated part of a bigger cloud network. Think of it as your own private section within a shared building, where you decide who gets in and out, and what can happen inside. This kind of setup is very helpful for systems that use many connected devices because it lets you build a very specific network just for them, which is pretty cool, actually.
This guide will walk you through the ideas behind setting up your own private network space for your connected devices. We will talk about why it makes sense to use this kind of network for your projects, and what steps you can take to get it all working. It’s about giving your devices a safe place to communicate, so you can feel more in control of your operations, and that's something we all want, isn't it?
- How To Use Remote Access Raspberry Pi Behind Router Mac
- Iot Remote Management Examples
- T%C3%BCrk Ifsa Sotwe
- Hikaru Nagi
- Pining For Kim By Trailblazer Link
Table of Contents
- What is a VPC, really?
- Why would you want a RemoteIoT VPC Tutorial setup?
- Getting Started- The RemoteIoT VPC Tutorial First Steps
- How do you keep things safe in your RemoteIoT VPC Tutorial?
- Connecting Your RemoteIoT Devices- A VPC Tutorial Insight
- What are some common hiccups with a RemoteIoT VPC Tutorial?
- Making it all work together- The RemoteIoT VPC Tutorial for Operations
- The Big Picture for Your RemoteIoT VPC Tutorial
What is a VPC, really?
A VPC is, in essence, your very own corner of a public cloud. It's like having a private room inside a big, busy office building. You get to decide who comes into your room and what goes on there, even though the building itself is shared by many different businesses. This private space has its own rules for how things connect and how information flows, so you have a lot of say over what happens, you know, inside your own little world.
When you set up a VPC, you get to pick your own range of internet addresses, which are like unique street numbers for devices. You also get to make sub-sections within your private area. These sub-sections are like different rooms in your private office, each with a specific purpose. For example, you might have one room for your web servers and another for your databases, keeping them separate for better organization and protection, which is pretty sensible, I mean.
The main idea behind a VPC is to give you a sense of being alone in the cloud, even when you are sharing the physical computer equipment with many others. It means your connected devices can talk to each other without their conversations mixing with traffic from other cloud users. This separation is a big deal for keeping your operations private and secure, as a matter of fact.
- What Is P2p In Iot With Example
- T%C3%BCrk If%C5%9Fa Sotwe
- Turk Ifsa Sotwe
- Pier Luigi Forlani
- Valentina Paloma Pinault
It also means you have a lot of say over how information moves around. You can set up specific pathways for data to travel, and you can put up digital walls to stop unwanted visitors. This level of control is something that helps a lot when you are dealing with sensitive information or critical operations, and that's usually the case with connected devices, isn't it?
So, in simple terms, a VPC is your personal, isolated network space within a larger cloud service. It offers a way to have your connected devices operate in a more controlled and protected environment, which is something many people find very appealing, particularly for important projects, as I was saying.
Why would you want a RemoteIoT VPC Tutorial setup?
One big reason to consider a private network for your connected devices is safety. When your devices are sending and receiving information, you want to be sure that only the right people and systems can access that information. A private cloud space helps you build a strong barrier against unauthorized access, which is something everyone wants for their data, right?
Imagine your connected devices are like valuable items in a store. You wouldn't just leave them out in the open for anyone to pick up. You'd put them behind a counter or in a display case. A private network does something similar for your digital items, creating a secure area where they can operate without being exposed to the wider internet, so it's a pretty good idea, generally.
Another benefit is having a lot of say over how your network behaves. You can set specific rules for how information travels between your devices and other services. This control means you can make sure your connected devices always perform as you expect, and that their interactions are predictable and reliable, which is quite important for any system, you know.
This level of control also helps with managing the addresses of your devices. You can assign them specific private addresses that are only visible within your private network. This helps keep things organized and makes it harder for outsiders to even know your devices exist, which is a big plus for keeping a low profile, as a matter of fact.
Then there's the idea of growing your operations. As you add more connected devices, you want a network setup that can grow with you without causing problems. A private cloud space is built to handle this kind of expansion. You can add more devices, more services, and more connections without having to rebuild your entire network from scratch, which is very convenient, if you ask me.
Also, some industries have very strict rules about how data is handled and stored. Using a private network can help you meet these rules more easily. Because you have so much control over the network environment, you can set things up to be in line with whatever regulations apply to your field, which is often a big concern for businesses, isn't it?
So, to sum it up, a private network for your connected devices gives you better safety, more say over how things work, the ability to grow without trouble, and help with following industry rules. These are all very good reasons to think about this kind of setup for your projects, and that's why many people choose to go this route, you know.
Getting Started- The RemoteIoT VPC Tutorial First Steps
To begin building your private network for connected devices, the first thing to think about is which cloud service provider you want to use. There are a few big names out there, and each one offers slightly different ways to set up your private space. It's a bit like choosing which company to get your internet from; they all do similar things, but their specific features and pricing might vary, so you might want to look around a little, you know.
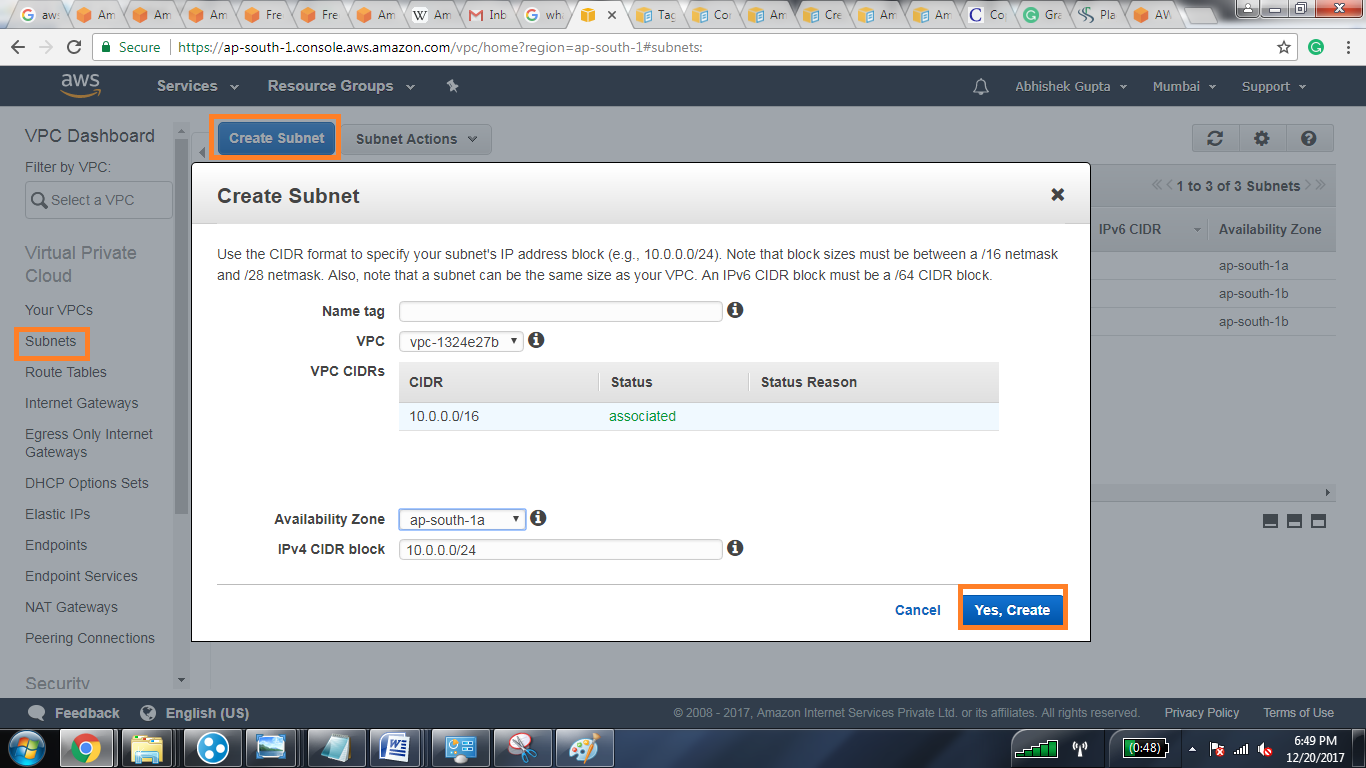
Once you have picked a cloud provider, the very next step is to create the private network itself. This usually involves going into the cloud provider's online control panel and finding the option to make a new private cloud. You'll give it a name, and then you'll need to decide on a range of internet addresses for it. This address range is like picking a specific block of street numbers for your private neighborhood, and it's a pretty important decision, as a matter of fact.
After you have your main private network set up, you will want to divide it into smaller sections. These are called sub-sections or subnets. Think of them as different districts within your private neighborhood. You might have one district for devices that need to talk to the outside world, and another district for devices that should only talk to each other, keeping them separate, which is usually a good idea.
It's often a good practice to create at least two kinds of sub-sections: public ones and private ones. Public sub-sections are for things that need to be reached from the internet, like a web server that collects data from your connected devices. Private sub-sections are for the devices themselves, or for databases, which should not be directly exposed to the internet, so that's a key distinction, really.
Setting up these sub-sections involves assigning them their own smaller ranges of internet addresses from the main range you picked earlier. This helps keep everything organized and makes it easier to control the flow of information. It's like having different zip codes within your private neighborhood, each with its own purpose, you see.
You will also need to think about how information moves between these sub-sections and how it gets in and out of your private network. This involves setting up what are called routing tables. These tables are like maps that tell information packets where to go, making sure they reach their intended destination within your private space, and that's something you really need to get right, basically.
For example, if a device in a private sub-section needs to send data to a service on the internet, the routing table will tell that data to go through a specific gateway that allows it to leave your private network. Without proper routing, your devices might not be able to communicate at all, which would be a bit of a problem, wouldn't it?
So, the starting point for your connected device network is choosing a cloud provider, making your main private network, dividing it into public and private sub-sections, and then setting up the pathways for information to travel. These initial steps lay the groundwork for a secure and functional environment for your devices, and they are quite important to get right, in a way.
How do you keep things safe in your RemoteIoT VPC Tutorial?
Once your private network is taking shape, a big part of keeping it secure involves setting up what are known as security groups. Think of security groups as personal firewalls for each of your devices or groups of devices. They decide what kind of information can come in and go out of those specific devices, which is pretty handy, you know.
For example, you might have a security group that only allows your connected devices to send data to a specific database, and nothing else. This means that even if someone manages to get inside your private network, they can't just access anything they want; they are still restricted by these digital walls, and that's a very good layer of protection, actually.
You can set up different security groups for different purposes. Maybe one group for your data-collecting devices, another for your control systems, and yet another for any servers that process the information. This way, you can apply very specific rules to each type of component, making your overall system much more secure, and that's a good approach, generally speaking.
Beyond security groups, there's another layer of protection called Network Access Control Lists, or NACLs. These are like gatekeepers for your entire sub-sections, rather than individual devices. While security groups filter traffic for a single device, NACLs filter traffic for a whole group of devices within a sub-section, which is a broader kind of control, you see.
NACLs can be set up to allow or block information based on its source or destination, and they apply to all traffic entering or leaving a sub-section. This means you have two chances to stop unwanted information: once at the sub-section level with NACLs, and then again at the individual device level with security groups, providing a very thorough defense, as a matter of fact.
Another important aspect of safety is managing who can do what within your cloud environment. This is where Identity and Access Management, or IAM, comes in. IAM lets you define specific roles and permissions for people or even for your connected devices themselves. It's about making sure that only authorized entities can perform certain actions, like changing network settings or accessing sensitive data, which is quite important, really.
For example, you might give a specific connected device a role that allows it only to write data to a particular storage service, but not to read from it or delete anything. This limits the potential damage if that device were ever compromised, because its permissions are very narrow, and that's a smart way to do things, in a way.
So, keeping your connected device network safe involves using security groups for individual device protection, NACLs for sub-section-wide filtering, and IAM for managing permissions. Together, these tools create a strong shield around your operations, giving you a lot of confidence in the safety of your data and devices, and that's something you really want, isn't it?
Connecting Your RemoteIoT Devices- A VPC Tutorial Insight
Once your private network space is ready, you need to think about how your actual connected devices will talk to it. Sometimes, these devices are out in the real world, far from your cloud setup. Getting them to communicate securely with your private network is a key step, and there are a few ways to make this happen, you know.
One common method involves using Virtual Private Networks, or VPNs. A VPN creates a secure, encrypted tunnel over the public internet between your device and your private network. It's like building a secret passage that only your device and your private network can use, so anyone else trying to listen in will just hear gibberish, which is pretty neat, actually.
You can set up a VPN connection from individual devices, or from a gateway device at a physical location where many of your connected devices are gathered. This ensures that all information traveling between your devices and your private cloud space is protected from prying eyes, which is a very good thing for sensitive data, as a matter of fact.
For situations where you need a very high level of performance and reliability, and you have a lot of data moving back and forth, you might consider something like a dedicated connection. This is a direct, private network line from your physical location to the cloud provider's network, bypassing the public internet entirely, so it's a very robust option, usually.
This kind of direct connection offers consistent speed and lower chances of interruption, which can be very important for time-sensitive operations or for systems that generate a huge amount of information. It's a bit like having your own private highway directly to your cloud, rather than using the busy public roads, and that's a big advantage for some, you see.
Then there are different types of gateways that help your devices connect. An internet gateway, for example, allows devices in your public sub-sections to talk to the internet. This is needed if your devices need to fetch updates or send data to services that are outside your private network, which is often the case, isn't it?
For devices in private sub-sections that need to connect to internet services without being directly exposed, you might use a NAT gateway. This allows devices to send outgoing information to the internet and receive responses, but it stops anything from the internet from directly starting a connection to them, providing another layer of security, which is quite clever, really.
So, getting your connected devices to communicate with your private network involves choices like VPNs for secure tunnels, dedicated connections for high performance, and various gateways to manage how information flows in and out. Each option serves a different need, allowing you to build a connection strategy that fits your project just right, and that's something you really want to think about, basically.
What are some common hiccups with a RemoteIoT VPC Tutorial?
Even with the best intentions, things can sometimes go a bit wrong when setting up a private network for your connected devices. One very common issue people run into is with their security rules. It's easy to accidentally block information that you actually want to allow, or to allow information that you meant to block, which can cause a lot of head-scratching, you know.
For instance, you might set up a security group that doesn't allow your connected devices to send data to your data storage service. Everything looks right, but the data just isn't getting through. This often means you need to go back and check your security group rules very carefully, making sure that the right types of information are allowed to pass, and that's usually the first place to look, as a matter of fact.
Another frequent problem is running out of internet addresses within your private network. When you first set up your private network, you pick a range of addresses. If your project grows very quickly and you add many more devices than you planned for, you might use up all the available addresses. This means new devices won't be able to connect, which is a bit of a snag, isn't it?
To avoid this, it's a good idea to plan for growth when you first choose your address range. Make it larger than you think you'll need right away, so you have plenty of room to expand. If you do run out, you might need to add another private network or make some changes, which can be a bit of work, you see.
Routing issues are also pretty common. Remember those maps that tell information where to go? If those maps are wrong, information can get lost or go to the wrong place. For example, a device might try to send data to the internet, but if the routing table doesn't point it to the correct internet gateway, the data just won't go anywhere, which is frustrating, really.
Troubleshooting routing problems often involves looking at the paths information is supposed to take and comparing them to what's actually happening. It's about tracing the journey of a piece of information and finding where it gets stuck or takes a wrong turn, and that can take a little bit of detective work, usually.
Sometimes, the problem isn't with your private network setup itself, but with the devices trying to connect to it. Make sure your connected devices are properly configured to use the network settings you've created. This includes their own internet address settings and any security certificates they might need to connect securely, which is often overlooked, in a way.
So, when things don't seem to be working as expected, it's often a good idea to check your security rules, make sure you have enough internet addresses, look at your routing tables, and confirm your devices are set up correctly. These are the usual suspects when it comes to hiccups with your connected device network, and knowing where to look can save you a lot of time, basically.
Making it all work together- The RemoteIoT VPC Tutorial for Operations
Once your private network for connected devices is up and running, you'll want to make sure it keeps working smoothly. This means keeping an eye on things and being ready to respond if something goes wrong. It's a bit like owning a car; you don't just drive it, you also check the oil and tires regularly, you know.
Monitoring your private network involves looking at things like how much information is flowing, whether there are any errors, and if all your connections are active. Cloud providers usually offer tools that let you see this kind of information on a dashboard. This helps you spot problems early, before they become big issues, which is very helpful, actually.
Logging is another important part of keeping things running well. This means recording all the important events that happen within your private network. For example, you might log every time a device connects, or every time information is sent to a specific service. These logs are like a diary of your network's activities, and they are very useful for figuring out what happened if something goes wrong, as a matter of fact.
You can set up alerts based on your monitoring and logs. If a certain condition is met, like if too much information is trying to get into your network from an unusual source, you can get a notification. This allows you to react quickly to potential problems, helping you maintain the security and performance of your connected device system, which is pretty important, isn't it?
For more advanced setups, you might even think about automating some of the tasks related to your private network. This could involve using scripts or special tools to automatically create new sub-sections, adjust security rules, or even set up new connections when you add more devices. Automation helps save time and reduces the chance of human error, which is a big plus, you see.
So, making your connected device network work well over time involves actively watching its performance, keeping detailed records of its activities, and setting up alerts for anything unusual. For those who want to go a step further, automating routine tasks can make managing your network even easier and more reliable, and that's something many people aim for, in a way.
- Speed Racers Brother
- P2p Iot Streaming
- Famous People From Long Island
- How Do You Access Raspberry Pi Device Remotely Using Mac
- Sone 436