Getting your Raspberry Pi to talk to you from anywhere, safely, is a big deal for many folks. It means you can check on things, send new instructions, or even just see if it's doing okay, even when you're far away. This kind of connection, especially for little gadgets like a Raspberry Pi that are part of the internet of things, brings up some questions about keeping everything private and sound. You want to be sure that only you, and perhaps a few trusted others, can get to your small computer, so it's a bit like having a very private conversation over a long distance, and you want to make sure no one else is listening in.
You might have wondered about how to get to your small computer without opening up a lot of potential risks. Maybe you've thought about whether your important bits of information could be seen by someone else if you're not careful. It's a bit like wanting to leave your house door unlocked for easy entry but still wanting all your valuables safe inside, which, you know, doesn't quite work. People often worry about sending confidential details, like financial papers, over the internet, and those same worries apply to getting into your little devices remotely. You want that sense of security, that feeling that your digital space is truly yours.
So, finding a good way to make sure your remote connections are solid, especially when you're dealing with sensitive stuff or just want peace of mind, is pretty important. We're going to chat about how things like peer-to-peer setups and secure shell tools can help you get to your Raspberry Pi from a distance, keeping things locked down and private. This approach is, in a way, about making sure your little device is always within your reach, but also well-protected from anyone who shouldn't be poking around. It's about having control and quiet confidence in your setup.
- T%C3%BCrk If%C5%9Fa Sotwe
- 50 Year Olds
- Was Racer X Speed Racers Brother
- Sotwe If%C5%9Fa T%C3%BCrk
- Best Remote Iot Device Management Platform
Table of Contents
- Introduction
- Why Does Remote Access Matter for Your Raspberry Pi?
- What is SSH and How Does it Help Securely Connect Remote IoT?
- The Peer-to-Peer Magic for Securely Connecting Remote IoT
- Getting Started - Setting Up Your Securely Connected Remote IoT P2P SSH
- What Are Some Common Worries When You Securely Connect Remote IoT?
- Keeping Things Tight - Extra Steps for Securely Connecting Remote IoT P2P SSH
- How to Securely Connect Remote IoT P2P SSH Without Hassle?
Why Does Remote Access Matter for Your Raspberry Pi?
Having the ability to get to your Raspberry Pi from somewhere else is, well, very handy. Think about it: your little computer might be sitting in a far-off spot, maybe monitoring a garden, controlling some lights, or even just acting as a tiny server for your home projects. If you need to make a change, check on its status, or grab some information, you don't want to have to physically go to where it is every single time. That would be, quite honestly, a bit of a pain. This is where the idea of securely connecting your remote IoT devices, like your Raspberry Pi, comes into play.
For small businesses, this can be even more important. Imagine having a device at a client's site that needs a quick update or a check-up. Being able to access it from your office, knowing the connection is safe, saves a lot of time and effort. It's similar to how you'd want to securely send important files to someone without worrying about them getting into the wrong hands. The convenience of remote access is huge, but that convenience absolutely needs to come with a strong sense of safety, so that your private information stays private and your system stays yours.
Without a proper way to get in, your tiny computer might just sit there, doing its job, but if something goes wrong, or if you need to adjust its tasks, you're stuck. A secure way to connect means you're always in charge, no matter the distance. It means you can, for instance, fix a problem with a program on your Raspberry Pi without needing to drive across town. This kind of control, when it's done with proper safeguards, makes your small projects or business setups much more useful and much less stressful to manage, which is, of course, a good thing.
- Pining For Kim Full Free
- Tlc Members
- Are Bamboo Shoots Healthy
- Remote Iot Device Management Platform
- Kim Kardashian And Damon Thomas
What is SSH and How Does it Help Securely Connect Remote IoT?
When we talk about securely connecting remote IoT devices, one of the first things that comes up is something called SSH. This stands for Secure Shell, and it's a way for your computer to talk to another computer, like your Raspberry Pi, over an unprotected network, but in a way that keeps everything private. It's like having a special, secret phone line where everything you say gets scrambled up so only the person on the other end can understand it. This scrambling, or encryption, is what makes it so useful for protecting your conversations and commands.
Think about sending a message to your Raspberry Pi telling it to turn on a light. If you just sent that command without any protection, someone else on the same network might be able to see it. That's not ideal, especially if you're sending more sensitive instructions or checking on private data. SSH helps make sure that when your Raspberry Pi and your computer are talking to each other, their chat is all scrambled up. It's like they're speaking in a secret code that only they can understand, so no one else can listen in on what they're saying. This keeps your information nice and private, which is, you know, a pretty big deal when you're dealing with things you don't want others to see.
So, when you use SSH to securely connect to your remote IoT Raspberry Pi, you're creating a private channel. Any commands you send, any files you move back and forth, they all go through this protected tunnel. This means that even if someone were to try and intercept your connection, all they'd see is a jumble of meaningless characters. It's a fundamental tool for making sure your remote interactions are kept just between you and your device, giving you a solid foundation for your remote activities. It really helps calm those worries about data being exposed, doesn't it?
The Peer-to-Peer Magic for Securely Connecting Remote IoT
Now, let's chat about something called P2P, or peer-to-peer, and how it fits into securely connecting your remote IoT devices. Usually, when you connect to something on the internet, you go through a central server. It's like making a phone call through a big phone company switchboard. But with P2P, your computer and your Raspberry Pi talk directly to each other. There's no middleman server involved, which can be pretty cool for a few reasons. It's a bit like two people having a direct walkie-talkie conversation rather than going through a large network hub.
For a small device like a Raspberry Pi, especially if it's sitting behind a home internet connection, direct connections can be a real benefit. Sometimes, getting into your Raspberry Pi from outside your home network can be tricky because of things like firewalls or how your internet provider sets things up. P2P methods often help get around these sorts of hurdles by finding a direct path between your computer and the Raspberry Pi. This can make setting up your remote access a good deal simpler, which is, frankly, a welcome relief for many people who just want things to work.
When you combine P2P with SSH for securely connecting your remote IoT Raspberry Pi, you get a powerful setup. The P2P part helps establish that direct line, making it easier to reach your device no matter where it is. Then, the SSH part jumps in to make sure everything sent over that direct line is scrambled and private. It's like having a secret, direct phone line to your Raspberry Pi that no one else can listen to. This combination offers a very private and often more straightforward way to manage your devices from a distance, without needing to mess with complicated network settings, which can be a real headache, as you might know.
Getting Started - Setting Up Your Securely Connected Remote IoT P2P SSH
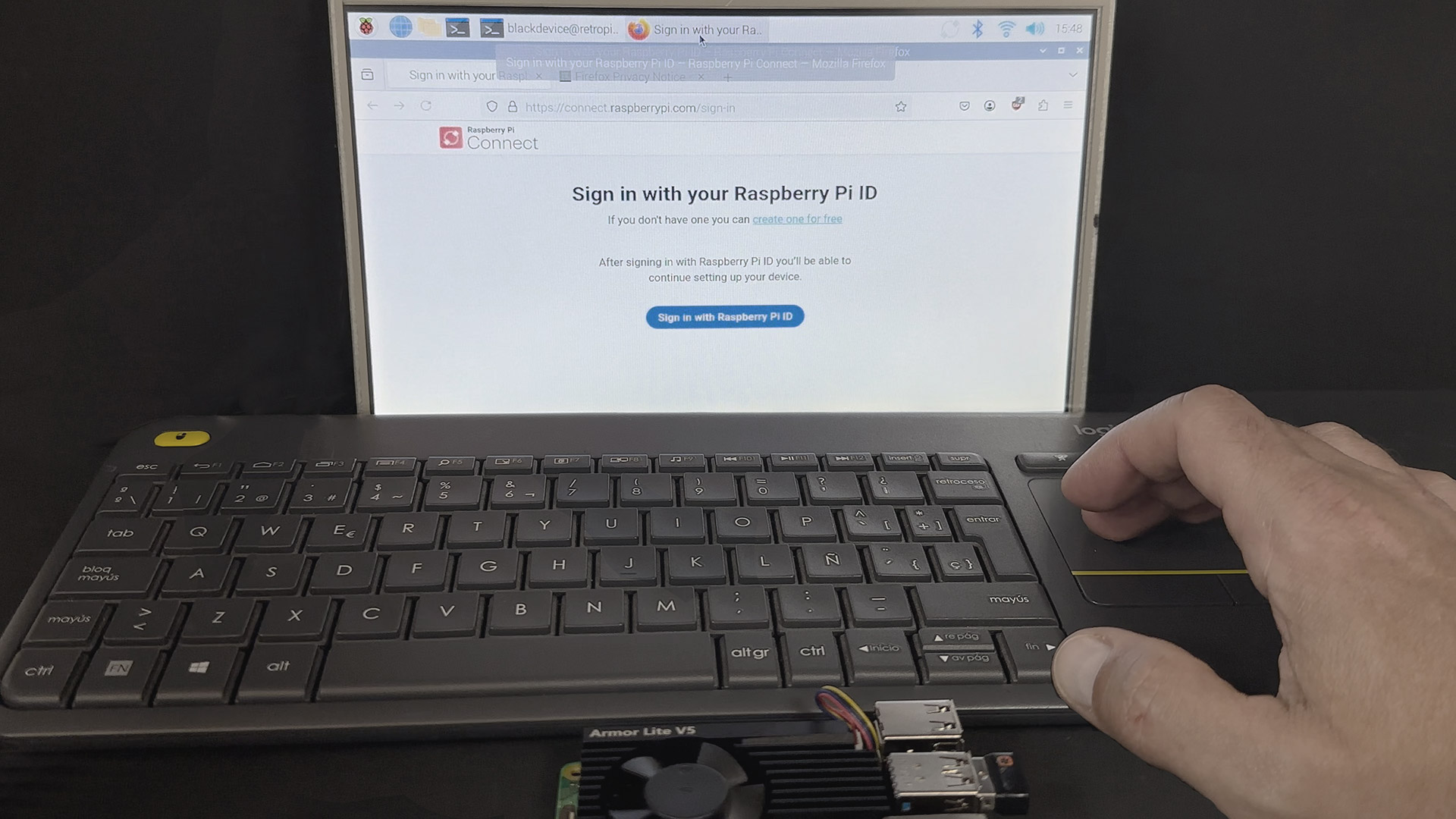
Getting your Raspberry Pi ready for securely connecting remotely using P2P and SSH involves a few steps, but they're pretty manageable. First off, you'll want to make sure SSH is turned on on your Raspberry Pi. This is usually a simple setting you can flip on, and it's the gateway to getting that private conversation going. You can often do this when you first set up your Raspberry Pi's operating system, or later on with a quick command. It’s like making sure your phone is set to receive calls before you give out your number.
Next, you'll want to think about how you're going to use SSH. While you can use passwords, a much safer way is to use something called SSH keys. These are like a pair of very special, unique digital keys – one stays on your computer, and the other goes on your Raspberry Pi. When you try to connect, they have a little secret handshake, and if the keys match, you're in. This is much harder for someone to guess than a password, making your securely connected remote IoT setup much more robust. It's a bit like having a lock that only opens with a very specific, one-of-a-kind key, rather than a combination someone might stumble upon.
For the P2P part, there are different tools and services that can help you create that direct connection without needing to open up specific "ports" on your home router, which can sometimes be a bit of a bother and a security worry. These tools help your Raspberry Pi and your computer find each other on the internet and then establish that direct, private link. They essentially handle the trickier network bits for you, so you can focus on what you want your Raspberry Pi to do. This simplifies the process quite a lot, actually, and makes it much more approachable for someone who isn't a network wizard, which is, honestly, most of us.
What Are Some Common Worries When You Securely Connect Remote IoT?
When you're trying to securely connect remote IoT devices, it's natural to have a few concerns. One common worry is about someone else getting access to your device. You want to be sure that only authorized people can send commands or pull information from your Raspberry Pi. This is very similar to how people worry about financial documents or other private files being uploaded securely; you need that assurance that the digital door is truly locked. It's a valid concern, and one that good security practices aim to address head-on, so you can feel at ease.
Another thing people often wonder about is whether their connection is truly private. Is the information they're sending back and forth actually scrambled up? Are there any weak spots where someone could peek in? These questions are quite similar to those that come up when you try to download something and your browser blocks it, saying the site uses "outdated or unsafe" security settings. You want to avoid those kinds of warnings and ensure your remote connection is using the very best, most current methods to keep things private. It's about having that peace of mind that your data is truly yours, and no one else's.
Sometimes, the connection itself can be a source of frustration. You might find that you "can't connect securely to this page," or that your settings aren't quite right. This can happen with remote IoT devices too. It's not just about setting things up, but also about making sure they stay working and secure over time. Things like keeping your software updated and checking your connection settings regularly can help prevent these kinds of headaches. It's a bit like making sure your car has its regular check-ups; it keeps everything running smoothly and safely, which is, of course, what you want for your remote connections.
Keeping Things Tight - Extra Steps for Securely Connecting Remote IoT P2P SSH
Beyond the basic setup, there are some extra things you can do to make your securely connected remote IoT P2P SSH setup even more solid. One very important step is to always use strong, unique passwords for your Raspberry Pi accounts, even if you're primarily using SSH keys. Think of it as having a really good backup lock on your digital door. Never use simple words or common number sequences; make them long and a bit jumbled. It's honestly one of the simplest and most effective ways to keep unwanted visitors out, and it's something you can do right away.
Another good idea is to regularly update your Raspberry Pi's software. Just like your phone or computer gets updates to fix problems and add new features, your Raspberry Pi's operating system and
- Dodi Fayed Last Words
- Is Bamboo Healthy To Eat
- Best Remote Iot Update
- What Is P2p In Iot With Example
- Remote Iot Management